Getting Ahead of the Curve: How the SWIFT Framework Will Transform Application Development
In a previous article, The Department of Defense's Digital Transformation: Transitioning from RMF to SWIFT, I explored the strategic implications and organizational considerations surrounding the adoption of the Software Fast Track (SWIFT) Framework as it prepares to replace the traditional Risk Management Framework (RMF). Building on that foundation, this article shifts focus to the practical implementation challenges and opportunities that development teams will face as they adapt to the SWIFT Framework requirements.
The SWIFT Framework represents more than just a change in compliance requirements—it's a complete reimagining of how security integrates with application development from the earliest stages through production deployment. Organizations that proactively adapt their development practices will gain significant competitive advantages, including faster time-to-market, reduced security vulnerabilities, and streamlined compliance processes.
Understanding the SWIFT Framework Revolution
Moving Beyond RMF Limitations
The Risk Management Framework, while foundational to cybersecurity governance, was designed for an era of monolithic applications and traditional deployment models. RMF's emphasis on periodic assessments, extensive documentation, and gate-based approvals creates bottlenecks that are incompatible with modern DevOps practices and continuous delivery requirements.
The SWIFT Framework addresses these limitations by introducing security as code, automated compliance validation, and continuous authorization principles that align naturally with modern application development practices. Instead of treating security as a checkpoint, SWIFT embeds security controls as integral components of the development pipeline.
Key transformation areas include:
- Automated security integration replacing manual assessments
- Risk-based continuous authorization instead of periodic reauthorization cycles
- Developer-centric security controls expressed as code
- Evidence-based compliance generated automatically through development activities
CI/CD Development: The Foundation of SWIFT Success
The transition to SWIFT Framework fundamentally depends on mature CI/CD implementations that can support integrated security automation. Organizations must evolve their development pipelines to accommodate continuous security validation while maintaining development velocity.
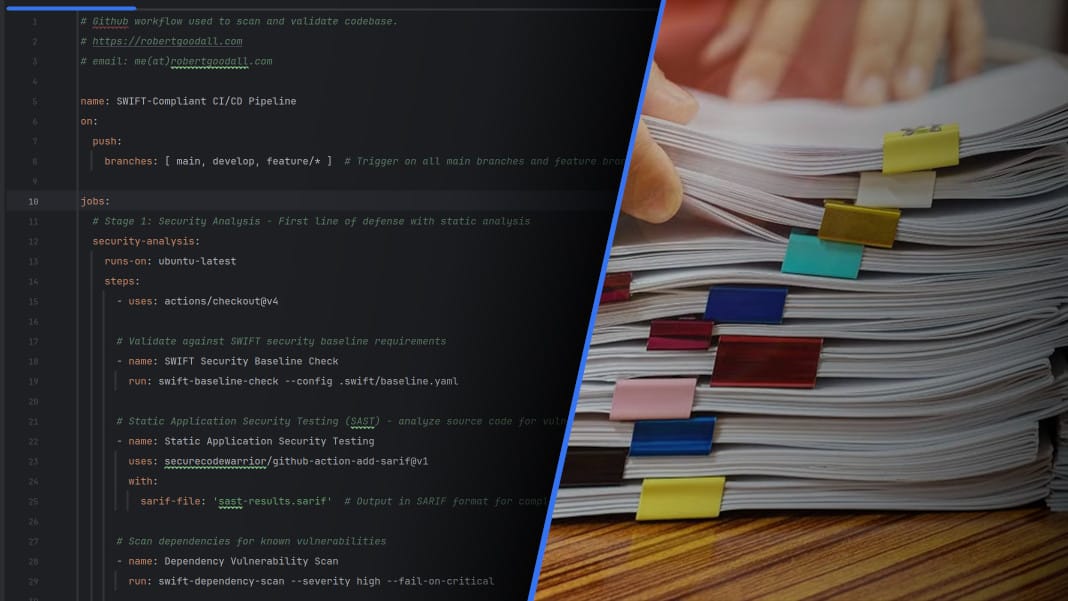
Example SWIFT-Compliant Pipeline
name: SWIFT-Compliant CI/CD Pipeline
on:
push:
branches: [ main, develop, feature/* ] # Trigger on all main branches and feature branches
jobs:
# Stage 1: Security Analysis - First line of defense with static analysis
security-analysis:
runs-on: ubuntu-latest
steps:
- uses: actions/checkout@v4
# Validate against SWIFT security baseline requirements
- name: SWIFT Security Baseline Check
run: swift-baseline-check --config .swift/baseline.yaml
# Static Application Security Testing (SAST) - analyze source code for vulnerabilities
- name: Static Application Security Testing
uses: securecodewarrior/github-action-add-sarif@v1
with:
sarif-file: 'sast-results.sarif' # Output in SARIF format for compliance
# Scan dependencies for known vulnerabilities
- name: Dependency Vulnerability Scan
run: swift-dependency-scan --severity high --fail-on-critical
# Scan Infrastructure as Code templates for security misconfigurations
- name: Infrastructure as Code Security
run: swift-iac-scan --framework terraform --baseline .swift/iac-baseline.yaml
# Stage 2: Dynamic Security Testing - Runtime security validation
security-testing:
runs-on: ubuntu-latest
needs: security-analysis # Only run after static analysis passes
steps:
- uses: actions/checkout@v4
# Dynamic Application Security Testing (DAST) - test running application
- name: Dynamic Application Security Testing
run: swift-dast-scan --target http://localhost:3000 --profile swift-baseline
# Validate API security against OpenAPI specification
- name: API Security Testing
run: swift-api-security-test --openapi ./api/swagger.yaml
# Scan container images for vulnerabilities and misconfigurations
- name: Container Security Scan
uses: aquasecurity/trivy-action@master
with:
image-ref: ${{ github.repository }}:${{ github.sha }}
format: 'swift-sarif' # SWIFT-compliant output format
# Stage 3: Compliance Validation - Generate evidence for SWIFT framework
swift-compliance:
runs-on: ubuntu-latest
needs: [security-analysis, security-testing] # Requires both security stages to complete
steps:
# Aggregate all security scan results into SWIFT evidence package
- name: Generate SWIFT Evidence Package
run: |
swift-evidence-generator \
--sast-results sast-results.sarif \
--dast-results dast-results.json \
--output swift-evidence-package.zip
# Validate security controls against SWIFT framework requirements
- name: SWIFT Control Validation
run: |
swift-control-validator \
--evidence swift-evidence-package.zip \
--baseline .swift/control-baseline.yaml \
--generate-ato-recommendation # Generate ATO recommendation
# Stage 4: Continuous Authorization - Automated ATO process for production
continuous-authorization:
runs-on: ubuntu-latest
needs: swift-compliance
if: github.ref == 'refs/heads/main' # Only run for main branch deployments
steps:
# Submit evidence package to SWIFT authorization system
- name: Submit for Continuous ATO
run: |
swift-ato-submit \
--evidence swift-evidence-package.zip \
--system-id ${{ secrets.SWIFT_SYSTEM_ID }} \
--auto-approve-low-risk # Automatically approve low-risk changes
Pipeline Security Integration
Modern CI/CD pipelines under the SWIFT Framework must integrate security checkpoints at every stage while maintaining development velocity. Each stage requires specific tooling to support comprehensive security validation:
Stage 1 - Security Analysis Tools:
- Static Application Security Testing (SAST): Tools like SonarQube, Checkmarx, or Veracode analyze source code for security vulnerabilities before runtime
- Dependency Scanning: Snyk, OWASP Dependency-Check, or GitHub Dependabot identify vulnerable third-party components
- Infrastructure as Code (IaC) Security: Checkov, Terrascan, or Bridgecrew scan Terraform/CloudFormation templates for misconfigurations
- Secret Detection: GitLeaks, TruffleHog, or GitHub Secret Scanning prevent hardcoded credentials from entering repositories
Stage 2 - Dynamic Security Testing Tools:
- Dynamic Application Security Testing (DAST): OWASP ZAP, Burp Suite Enterprise, or Rapid7 AppSpider test running applications for runtime vulnerabilities
- API Security Testing: Postman Security, 42Crunch, or Salt Security validate API endpoints against security specifications
- Container Security: Aqua Trivy, Twistlock, or Anchore scan container images for vulnerabilities and compliance violations
- Interactive Application Security Testing (IAST): Contrast Security or Hdiv provide real-time security feedback during testing
Stage 3 - Compliance and Evidence Generation:
- Policy as Code: Open Policy Agent (OPA), Falco, or AWS Config Rules enforce security policies automatically
- Compliance Automation: Chef InSpec, AWS Security Hub, or Nessus validate security controls against frameworks
- Evidence Collection: Drata, Vanta, or custom scripts aggregate security artifacts for compliance reporting
- Risk Assessment: RiskLens, Resolver, or ServiceNow GRC calculate risk scores based on security findings
Stage 4 - Continuous Authorization Tools:
- Security Orchestration: Phantom, Demisto, or custom workflows coordinate security tool outputs
- Continuous Monitoring: Splunk, Datadog Security, or AWS CloudTrail provide real-time security visibility
- Automated Response: PagerDuty, Opsgenie, or custom webhooks trigger incident response workflows
- Authorization Management: Custom SWIFT-compliant systems track authorization status and renewal requirements
Key Integration Principles:
- Security Gates as Code: Automated security gates enforce SWIFT compliance requirements through policy-as-code implementations
- Parallel Security Processing: Security scans run in parallel with functional testing to minimize pipeline execution time
- Fail-Fast Security Validation: Critical security violations halt the pipeline immediately
- Automated Remediation Workflows: Pipelines automatically remediate common security issues when possible
Shift-Left Security: Transforming Development Culture
Early Security Integration
The shift-left security paradigm, central to SWIFT Framework success, fundamentally changes when and how security considerations enter the development process:
IDE-Integrated Security: Development environments integrate real-time security feedback directly into the coding experience, providing immediate visibility into potential security issues as code is written.
Security-Aware Design Patterns: Development teams must adopt security-aware design patterns and architectural principles that inherently reduce security risks rather than addressing them as afterthoughts.
Threat Modeling Automation: Traditional threat modeling processes are augmented with automated tools that analyze application architecture and identify potential security concerns during the design phase.
Developer Security Empowerment
The SWIFT Framework requires developers to take greater ownership of security outcomes, supported by integrated tooling throughout the development process:
IDE-Integrated Security Tools:
- Real-time Code Analysis: Extensions like SonarLint, Snyk Code, or GitHub Copilot provide immediate security feedback as developers write code
- Security Linting: ESLint security plugins, Bandit for Python, or SpotBugs for Java catch common security issues during development
- Vulnerability Intelligence: IDE plugins from Veracode, Checkmarx, or WhiteSource surface vulnerability information directly in the development environment
Developer Security Testing Tools:
- Unit Testing Frameworks: Security-focused unit tests using frameworks like OWASP SecurityUnit or custom security test suites
- Local Security Scanning: Pre-commit hooks with tools like Gitleaks, Semgrep, or local Snyk scans prevent security issues from entering repositories
- Security Code Review: Tools like CodeQL, SonarQube pull request analysis, or Reviewboard with security checklists
Security Learning and Training Platforms:
- Gamified Security Training: Platforms like Secure Code Warrior, HackerOne CTF, or SANS Secure Coding provide hands-on security education
- Vulnerability Databases: Access to CVE databases, OWASP Top 10 resources, and platform-specific security guides
- Internal Security Resources: Wiki systems, Confluence spaces, or custom portals with organization-specific security guidance
Core Developer Security Competencies:
- Security Coding Standards: Establish and enforce security coding standards with automated enforcement through linting and code review tools
- Security Testing Competency: Developers must develop competency in security testing techniques and vulnerability remediation
- Security Tool Proficiency: Teams must become proficient with security tools integrated into their development workflows
Cultural Transformation
Successfully implementing shift-left security requires deliberate cultural transformation:
- Security Champions Programs: Establish security champions within development teams who serve as local experts and advocates
- Blameless Security Culture: Foster a culture where security issues are treated as learning opportunities rather than blame assignments
- Security Metrics Integration: Integrate security metrics into development team performance indicators
Continuous Application Development Security Checks
Real-Time Security Validation
The SWIFT Framework's emphasis on continuous authorization requires real-time security validation throughout the development lifecycle, supported by comprehensive tooling ecosystems:
Continuous Security Monitoring Tools:
- Runtime Application Self-Protection (RASP): Contrast Security, Sqreen, or Hdiv provide real-time application security monitoring and blocking
- Application Performance Monitoring (APM) with Security: New Relic Security, Datadog Security Monitoring, or Dynatrace Security provide security insights within performance data
- Container Runtime Security: Aqua Security, Sysdig Falco, or Twistlock monitor container behavior for security anomalies
- Infrastructure Monitoring: Wazuh, OSSEC, or cloud-native tools like AWS GuardDuty provide infrastructure-level security monitoring
Code Commit Security Validation:
- Pre-commit Hooks: Git hooks with tools like pre-commit framework, Husky, or custom scripts that run security checks before code commits
- Commit Signing: GPG signature validation, GitHub commit verification, or similar tools ensure code authenticity
- Branch Protection: GitHub branch protection rules, GitLab push rules, or Bitbucket branch permissions enforce security policies
- Automated Security Reviews: GitHub Security Advisories, GitLab Security Dashboard, or custom security review automation
Configuration and Drift Detection:
- Configuration Management: Ansible, Puppet, or Chef with security modules ensure consistent security configurations
- Drift Detection: AWS Config, Azure Policy, or Google Cloud Security Command Center monitor configuration changes
- Policy Enforcement: Open Policy Agent (OPA), Gatekeeper, or cloud-native policy engines enforce security standards
- Compliance Monitoring: Chef InSpec, AWS Systems Manager Compliance, or custom compliance validation scripts
Behavioral Analysis and Threat Detection:
- User and Entity Behavior Analytics (UEBA): Splunk UBA, Microsoft Sentinel, or Exabeam detect unusual application behavior patterns
- Application Security Monitoring: Contrast Assess, Checkmarx Interactive, or Veracode Dynamic Analysis provide runtime security insights
- Threat Intelligence Integration: MISP, ThreatConnect, or commercial threat feeds enhance security monitoring with current threat data
- Incident Response Automation: Phantom, Demisto, or custom SOAR platforms automate response to security events
Key Security Validation Principles:
- Code Commit Security Hooks: Every code commit triggers automated security analysis that provides immediate feedback on introduced security issues
- Dynamic Security Monitoring: Applications include embedded security monitoring that continuously assesses runtime security posture
- Configuration Drift Detection: Automated monitoring detects when deployed applications drift from approved security configurations
Automated Compliance Evidence Generation
One of SWIFT Framework's most significant advantages is the automated generation of compliance evidence through normal development activities:
- Continuous Control Assessment: Security controls are continuously assessed and validated through automated processes
- Audit Trail Automation: Development activities automatically generate detailed audit trails that satisfy compliance requirements
- Evidence Correlation: Automated systems correlate evidence from multiple sources to provide comprehensive compliance pictures
- Risk Assessment Integration: Continuous risk assessment processes update authorization decisions based on changing application characteristics
Getting Ahead of the Curve: Implementation Strategy
Phased Adoption Approach
Organizations should implement SWIFT Framework alignment through a carefully planned, phased approach:
Phase 1: Foundation Building: Establish basic CI/CD capabilities, implement fundamental security tooling, and begin cultural transformation through training and security champion programs.
Phase 2: Security Integration: Integrate security tools into CI/CD pipelines, implement basic shift-left practices, and establish automated security validation workflows.
Phase 3: Continuous Authorization: Implement continuous monitoring, automated compliance evidence generation, and real-time risk assessment capabilities.
Phase 4: Advanced Automation: Deploy advanced security automation, behavioral analysis, and fully integrated security orchestration platforms.
Technology Investment Priorities
Strategic technology investments should focus on capabilities that provide maximum impact:
- Unified DevSecOps Platform: Invest in platforms that integrate development, security, and operations tooling into cohesive workflows
- Cloud-Native Security: Prioritize cloud-native security solutions that align with modern application architectures
- API-First Security Tools: Choose security tools with robust APIs that enable integration with existing development toolchains
- Scalable Monitoring Infrastructure: Implement monitoring infrastructure that can scale with application growth
Organizational Readiness
Successful SWIFT Framework adoption requires organizational changes that extend beyond technology implementation:
- Cross-Functional Team Formation: Create teams that include development, security, and operations personnel working toward shared objectives
- Skills Development Programs: Implement comprehensive skills development programs that prepare teams for increased security responsibilities
- Process Reengineering: Reengineer development and security processes to eliminate handoffs and reduce cycle times
- Leadership Alignment: Ensure leadership understanding and support for the cultural and process changes required
Measuring Success
Track specific metrics that demonstrate progress toward SWIFT Framework readiness:
- Security Integration Metrics: Measure the percentage of development activities that include integrated security validation
- Development Velocity Metrics: Monitor development cycle times and deployment frequency to ensure security integration doesn't negatively impact productivity
- Compliance Automation Metrics: Track the percentage of compliance evidence generated automatically
- Risk Reduction Metrics: Measure reduction in security vulnerabilities reaching production
Conclusion
The transition from RMF to the SWIFT Framework represents a fundamental shift in how organizations approach cybersecurity in application development. This transformation offers unprecedented opportunities for organizations that proactively adapt their development practices, but also presents significant challenges for those who delay preparation.
Success requires investing in CI/CD maturity, embracing shift-left security principles, and implementing continuous security validation throughout the development lifecycle. Organizations that get ahead of this curve will find themselves with significant competitive advantages: faster time-to-market, reduced security risks, and improved development team satisfaction.
However, the window for proactive preparation is limited. As SWIFT Framework requirements become mandatory, organizations that have not prepared will face the challenge of transforming their development practices under pressure while competing with organizations that have already realized the benefits.
The time to begin this transformation is now. The question remains: will your organization be among the leaders who shape the future of secure application development, or will you be left scrambling to catch up as the industry moves forward without you?




